|
| Secret Center Usage |
| Step 2. Testing Secret Center application |
|
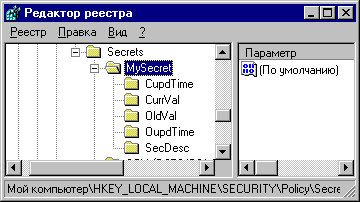
Run our example, enter the 'MySecret' text into first edit and an arbitrary string into second edit. Press 'Write' button. The secret is stored now! To ensure in it restart our application, enter 'MySecret' text into first edit and press the 'Read' button. Your text should appear in the second edit. If it does not occur check that you have admin rights on your computer. These rights are necessary for this and all other examples. You can use any name for your secret instead of MySecret. Try to do it. Well, you see that our example works. But now the question arises: where the secret is stored? Is it possible to steal it? Who could steal it and how it could be done? Do not try to find the secret text on disk - you will not find it, it is encrypted and stored in... registry! To ensure in it we shall do a small trick that will allow us to browse secure registry parts. Look on you computer time (11:05 for example) and type in the command line the following command at 11:06 /interactive regedit.exe Of course you should substitute your own time into this command. Usually scheduler service is installed into LocalSystem account (check it and change if necessary!) so in a minute after this command scheduler will start registry editor with system rights. Be accurate! In this mode you have almost unlimited rights on registry. Registry corruption can damage your system easy. Do not modify any registry keys and/or values. It is not required for our tests. Go to the HKEY_LOCAL_MACHINE\SECURITY\Policy\Secrets\ key. As you see there is a subkey MySecret!
It's value is stored here. If you see other subkeys it means that there are some other secrets on your computer. Note, that you can't read secret values because they are encripted but you can read secret names. It allows you to read the secret values too. Use our example to ensure in it. So this trick gives you a possibility to know ALL NT secrets stored on your computer. It is interesting enough because NT have no functions that allows to enumerate secret names. Another conclusion: the administrator (and services in LocalSystem account too) can read all secrets stored in such manner while ordinary users can't do it. So NT secret storage does not protect data absolutely but protection is strong enough. How to use it? It depends on your needs. Windows NT stores DCOM passwords here for example. See the DCOM configuration example for details. |
| << | Index | Step 1 | Step 2 |
| Add your comment | Read comments |
| © 1998-2001
Alexey Dynnikov |
|